How To Plan A Security System
How To Develop Implement A Network Security Plan The objective of system security planning is to improve protection of information system resources. all federal systems have some level of sensitivity and require protection as part of good management practice. the protection of a system must be documented in a system security plan. Guide for developing security plans for federal information systems. the objective of system security planning is to improve protection of information system resources. all federal systems have some level of sensitivity and require protection as part of good management practice.

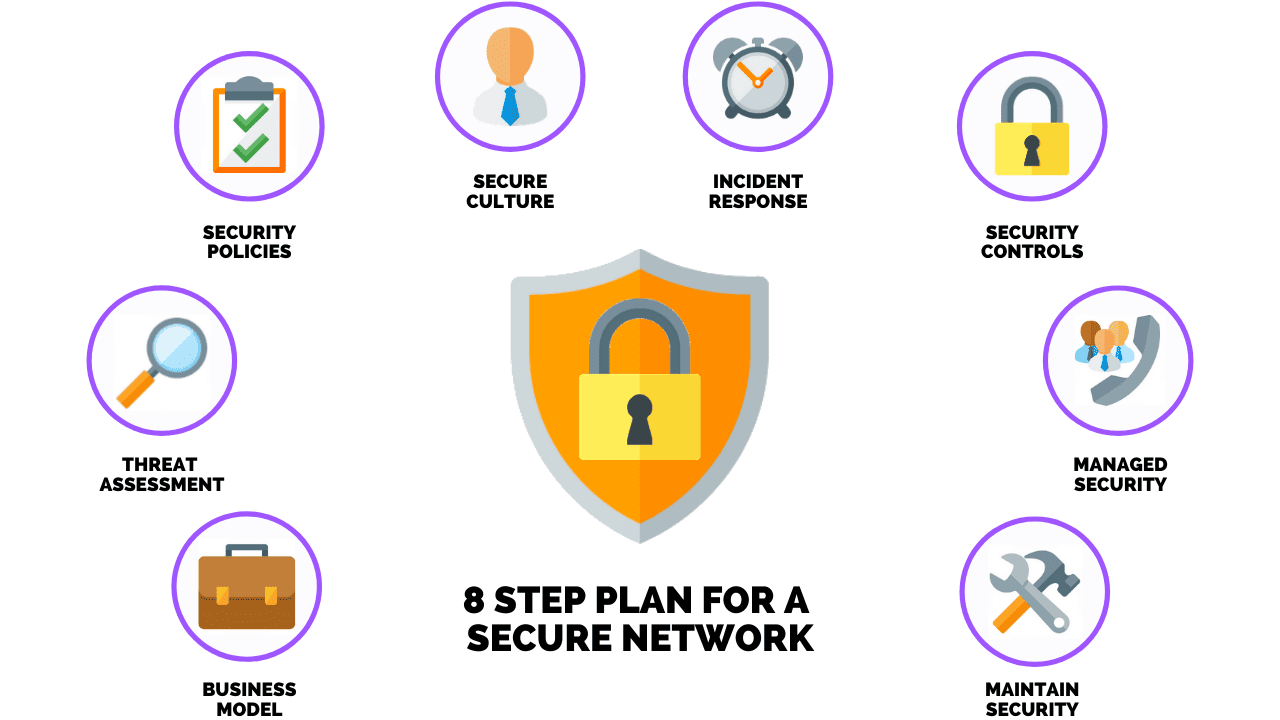
Nist Sp 800 171 Cmmc System Security Plan Toolkit Ckss Cybersecurity Solutions Learn what a system security plan (ssp) is and how to create one for nist 800 171 compliance. discover key steps and what you should include in your ssp. What is a system security plan (ssp)? a system security plan (ssp) is a comprehensive summary of the myriad security related elements of an individual information system (is) that manages information resources (ir). this includes all the system’s hardware, software, relevant personnel, etc. How to prepare a system security plan, with template to help keep your systems and applications secure, a system security plan is essential. learn how to create a plan and keep it up to date. There are 8 steps to developing and implementing an effective network security plan include: understanding your business model. performing a threat assessment. develop it security policies and procedures. creating a “security first” company culture. defining incident response. implementing security controls. working with a virtual ciso (vciso).

Have You Implemented A Security Plan For Your Business How to prepare a system security plan, with template to help keep your systems and applications secure, a system security plan is essential. learn how to create a plan and keep it up to date. There are 8 steps to developing and implementing an effective network security plan include: understanding your business model. performing a threat assessment. develop it security policies and procedures. creating a “security first” company culture. defining incident response. implementing security controls. working with a virtual ciso (vciso). Here are 5 key steps you can take to build your company’s system security plan and demonstrate how you intend to comply with all nist 800 171 security controls. who is responsible? nist 800 171 standards apply to any company that handles potentially sensitive information. Determine what aspects of your cybersecurity program have yet to be implemented and chart a course of action to get the program fully up and running. this course of action is called a plan of actions and milestones (poa&m) in cybersecurity parlance. we’ll discuss poa&ms next week. All federal systems have some level of sensitivity and require protection as part of good management practice. the protection of a system must be documented in a system security plan. Developing a new system security plan starts by evaluating your current security and its strengths and weaknesses. if you’ve faced any security threats recently, what caused them? how were they resolved? during this stage, identify all the physical and informational assets your system security needs to protect.
System Security Plan Template Here are 5 key steps you can take to build your company’s system security plan and demonstrate how you intend to comply with all nist 800 171 security controls. who is responsible? nist 800 171 standards apply to any company that handles potentially sensitive information. Determine what aspects of your cybersecurity program have yet to be implemented and chart a course of action to get the program fully up and running. this course of action is called a plan of actions and milestones (poa&m) in cybersecurity parlance. we’ll discuss poa&ms next week. All federal systems have some level of sensitivity and require protection as part of good management practice. the protection of a system must be documented in a system security plan. Developing a new system security plan starts by evaluating your current security and its strengths and weaknesses. if you’ve faced any security threats recently, what caused them? how were they resolved? during this stage, identify all the physical and informational assets your system security needs to protect.

Security System Plan How To Plan Floor Plans Emergency Plan All federal systems have some level of sensitivity and require protection as part of good management practice. the protection of a system must be documented in a system security plan. Developing a new system security plan starts by evaluating your current security and its strengths and weaknesses. if you’ve faced any security threats recently, what caused them? how were they resolved? during this stage, identify all the physical and informational assets your system security needs to protect.
Maintaining The Accuracy Of A System Security Plan Cential
Comments are closed.