Identity And Access Management Iam In Amazon Web Services Aws

Aws Identity And Access Management Fundamentals Use aws identity and access management (iam) to manage and scale workload and workforce access securely supporting your agility and innovation in aws. set and manage guardrails with broad permissions, and move toward least privilege by using fine grained access controls for your workloads. Describes how to control access to your aws resources by using aws identity and access management (iam) principals and then using policies to grant permissions in your aws account.
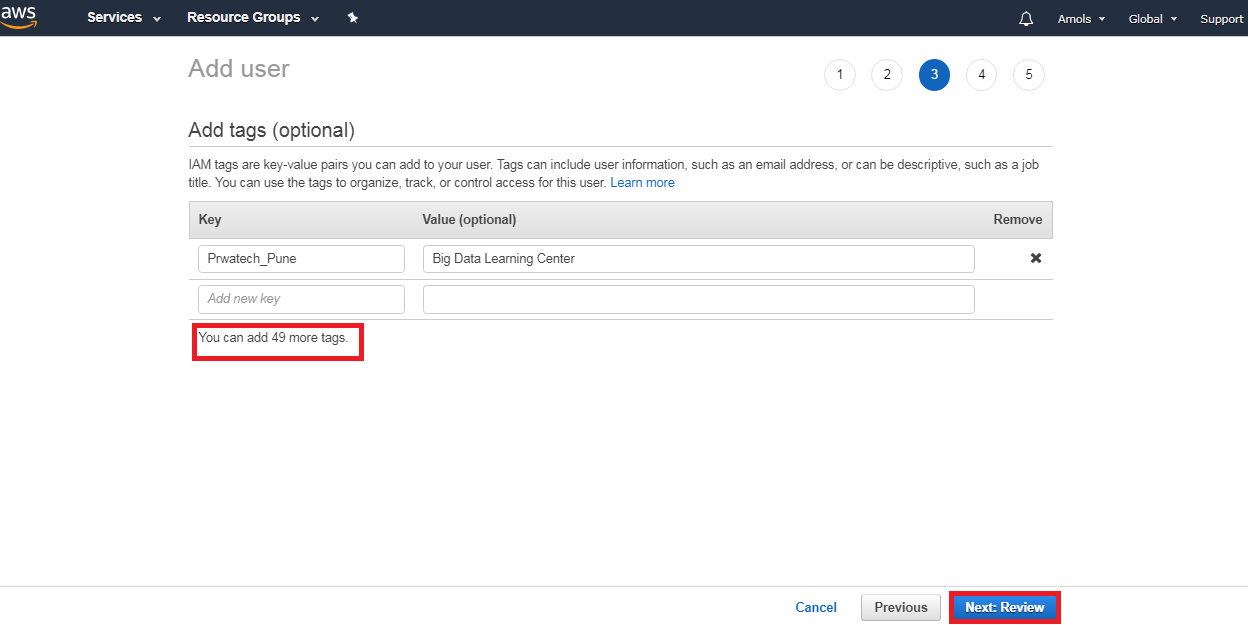
What Is Aws Identity And Access Management Iam Prwatech The most common method is through the aws management console, a web based interface that allows you to perform a wide range of iam administrative tasks, from creating users and roles to configuring permissions. This guide introduces you to iam by explaining iam features that help you apply fine grained permissions in aws. the guide shows you how to grant access by defining and applying iam policies to roles and resources. Learn how aws identity services enable you to securely manage identities, resources, and permissions at scale. Iam roles anywhere is a feature of aws identity and access management (iam) that enables you to use x.509 certificates from your public key infrastructure (pki) to request temporary amazon web services (aws) security credentials.
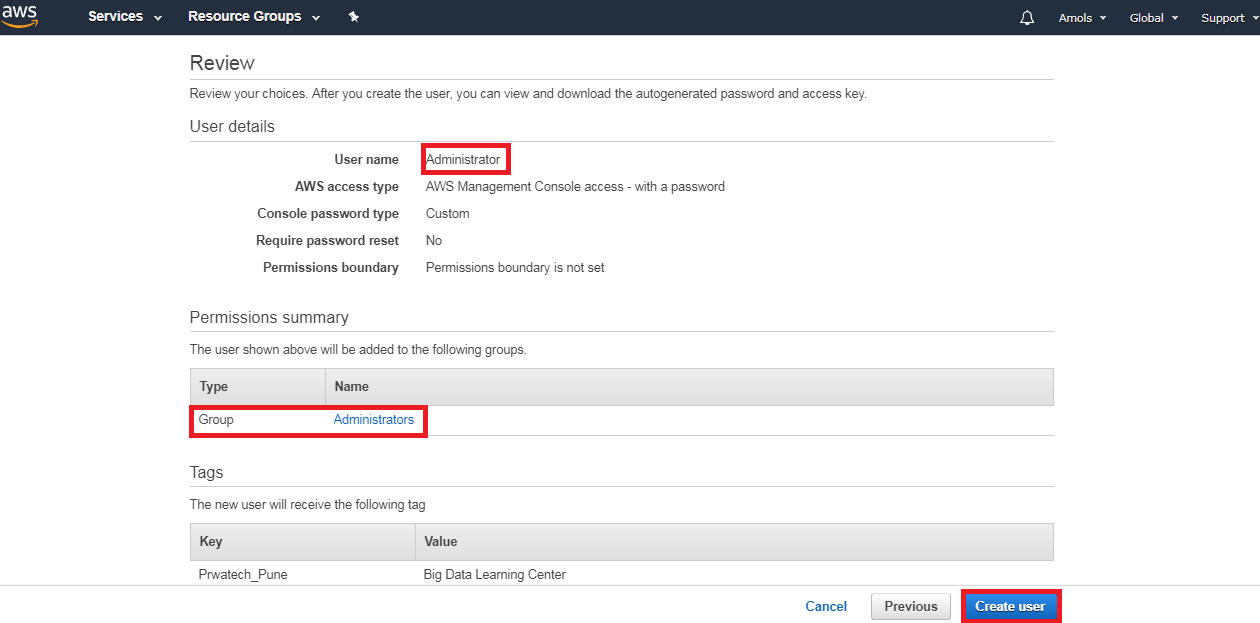
What Is Aws Identity And Access Management Iam Prwatech Learn how aws identity services enable you to securely manage identities, resources, and permissions at scale. Iam roles anywhere is a feature of aws identity and access management (iam) that enables you to use x.509 certificates from your public key infrastructure (pki) to request temporary amazon web services (aws) security credentials. For centralized access management, we recommend that you use aws iam identity center (iam identity center) to manage access to your accounts and permissions within those accounts. Aws identity and access management is a powerful tool for securely managing access to your aws resources. one of the primary benefits of using iam is the ability to grant shared access to your aws account. Iam provides fine grained access control across all of aws. with iam, you can control access to services and resources under specific conditions. use iam policies to manage permissions for your workforce and systems to ensure least privilege. iam is offered at no additional charge. for more information, see what is iam?. Aws identity and access management (iam) is a web service that helps you securely control access to aws resources. with iam, you can manage permissions that control which aws resources users can access.
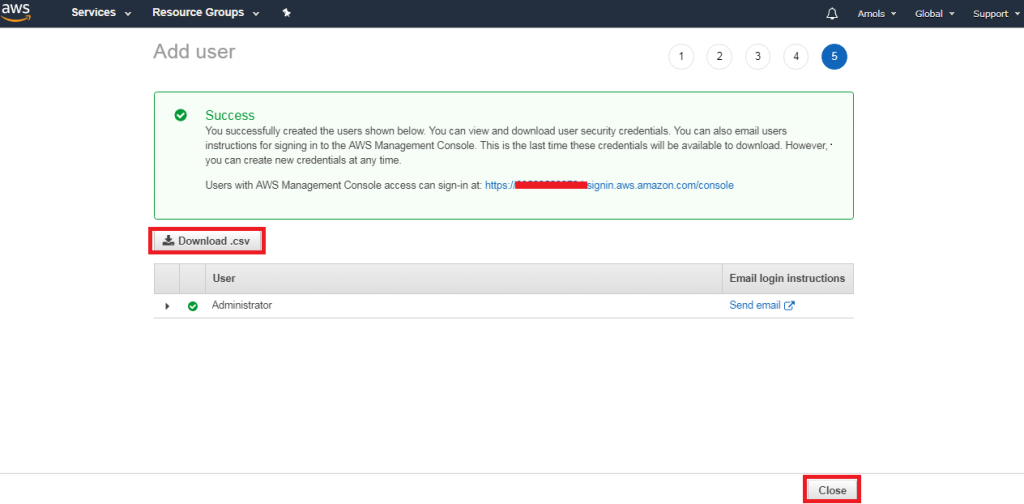
What Is Aws Identity And Access Management Iam Prwatech For centralized access management, we recommend that you use aws iam identity center (iam identity center) to manage access to your accounts and permissions within those accounts. Aws identity and access management is a powerful tool for securely managing access to your aws resources. one of the primary benefits of using iam is the ability to grant shared access to your aws account. Iam provides fine grained access control across all of aws. with iam, you can control access to services and resources under specific conditions. use iam policies to manage permissions for your workforce and systems to ensure least privilege. iam is offered at no additional charge. for more information, see what is iam?. Aws identity and access management (iam) is a web service that helps you securely control access to aws resources. with iam, you can manage permissions that control which aws resources users can access.
Comments are closed.