Solved Exercise 7 Consider The Following Aes S Box Used In Chegg Com

Solved Exercise 7 Consider The Following AES S-box Used In | Chegg.com
Solved Exercise 7 Consider The Following AES S-box Used In | Chegg.com Our expert help has broken down your problem into an easy to learn solution you can count on. here’s the best way to solve it. aes is a variant of the rijndael block cipher developed by two belgian cryptographers, vincent rijmen and joan daemen, who submitted a proposal to nist during the aes selection process.rijndael is a family of ciphers w …. A) to determine the possible output block from the given input block, you would need to apply the aes s box substitution to each of the bytes in the input block. for each input byte, you would look up the corresponding output byte in the aes s box provided above.

Consider The Following AES S-box Used In The ByteSub | Chegg.com
Consider The Following AES S-box Used In The ByteSub | Chegg.com Des is a block cipher intended to replace aes for commercial applications. the nonlinearity of the s box is due to the use of the multiplicative inverse. virtually all encryption algorithms, both conventional and public key, involve arithmetic operations on integers. For this question, consider the hill cipher given in the textbook on alphabet consisting of 26 english characters (a z), 10 numeric characters (0 9), and the following special characters, which correspond to integers t0 40. How to make the truth table of s box? if we want to build table 7 or it's binary equivalent above from scratch (rather than using the values in table 7 given in the standard), we can apply the definition of the s box as stated in fips 197 section 5.1.1. The s box used in aes is standardized and documented in cryptographic literature, confirming that the values derived from the inputs are accurate according to the aes specification.

Solved Consider The Following AES S-box Used In The Byte Sub | Chegg.com
Solved Consider The Following AES S-box Used In The Byte Sub | Chegg.com How to make the truth table of s box? if we want to build table 7 or it's binary equivalent above from scratch (rather than using the values in table 7 given in the standard), we can apply the definition of the s box as stated in fips 197 section 5.1.1. The s box used in aes is standardized and documented in cryptographic literature, confirming that the values derived from the inputs are accurate according to the aes specification. The s boxes are a system that is used in symmetric cryptographic algorithms to substitute and obscure the relationship between the key and the text that you want to cypher. Needs grading what is the output of the aes subbytes s box given the input 7e? figure 7. s box: substitution values for the byte xy (in hexadecimal format). not the question you’re looking for? post any question and get expert help quickly. To review the overall structure of aes and to focus particularly on the four steps used in each round of aes: (1) byte substitution, (2) shift rows, (3) mix columns, and (4) add round key. I am looking to understand how to answer this question from my class: find below the s box of aes. given the input 01010011 in binary, calculate the output.
Solved 4. [AES S-boxes] For AES, Compute The Respective | Chegg.com
Solved 4. [AES S-boxes] For AES, Compute The Respective | Chegg.com The s boxes are a system that is used in symmetric cryptographic algorithms to substitute and obscure the relationship between the key and the text that you want to cypher. Needs grading what is the output of the aes subbytes s box given the input 7e? figure 7. s box: substitution values for the byte xy (in hexadecimal format). not the question you’re looking for? post any question and get expert help quickly. To review the overall structure of aes and to focus particularly on the four steps used in each round of aes: (1) byte substitution, (2) shift rows, (3) mix columns, and (4) add round key. I am looking to understand how to answer this question from my class: find below the s box of aes. given the input 01010011 in binary, calculate the output.
Solved Using AES, Answer These Questions Given: Plaintext= | Chegg.com
Solved Using AES, Answer These Questions Given: Plaintext= | Chegg.com To review the overall structure of aes and to focus particularly on the four steps used in each round of aes: (1) byte substitution, (2) shift rows, (3) mix columns, and (4) add round key. I am looking to understand how to answer this question from my class: find below the s box of aes. given the input 01010011 in binary, calculate the output.
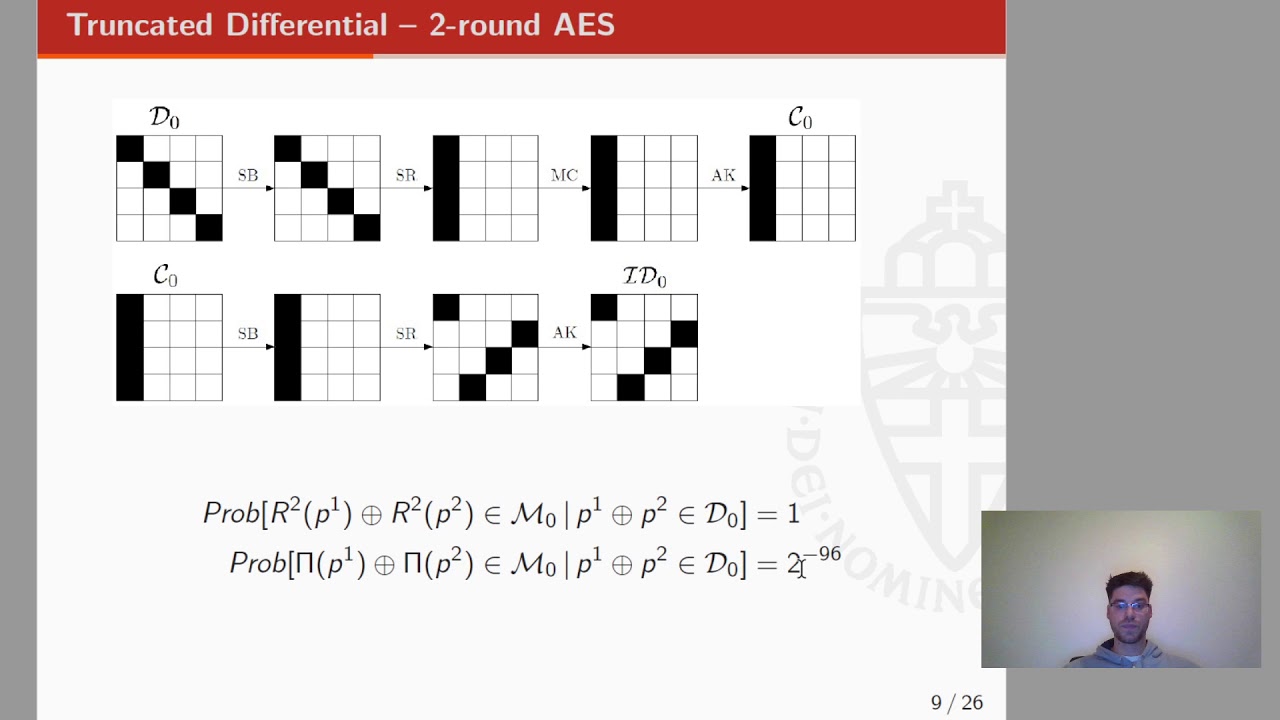
Mixture Integral Attacks on Reduced-Round AES with a Known/Secret S-Box
Mixture Integral Attacks on Reduced-Round AES with a Known/Secret S-Box
Related image with solved exercise 7 consider the following aes s box used in chegg com
Related image with solved exercise 7 consider the following aes s box used in chegg com
About "Solved Exercise 7 Consider The Following Aes S Box Used In Chegg Com"












Comments are closed.